Welcome back to the wireless series! As a continuation from our Explorations into Wi-Fi6/E, we're going to discuss wardriving. Wardriving has its roots in wardialing - scanning the numeric space of a set of telephone numbers to identify connections to equipment such as modems, fax machines, or other systems that may be interesting to manipulate for various purposes. Warwalking, warchalking, and wardriving all began as ways to identify and map the location of unsecured Wi-Fi networks or networks with vulnerabilities for later exploitation. These days, there is an entire community around wardriving that has turned it into a hobby to map not only Wi-Fi, but also Bluetooth, BLE, and cellular signals.
A Little Wigle
Thanks to the proliferation of wardriving as a hobby, we now have a large database publicly available which allows us to search for signals in a given location. This database, known as Wigle, is user-friendly and community supported. Anyone can upload signal data - there's even an Android app. Now, we won't be providing an instructional section on using the platform. However, we would like to point out a couple of interesting features that can assist with your next wireless pentest, red team, or any other assessment involving signal data.
First up is the Only Nets I Was the First to See feature. This, as it says, allows you to search for networks that you discovered in a given area.
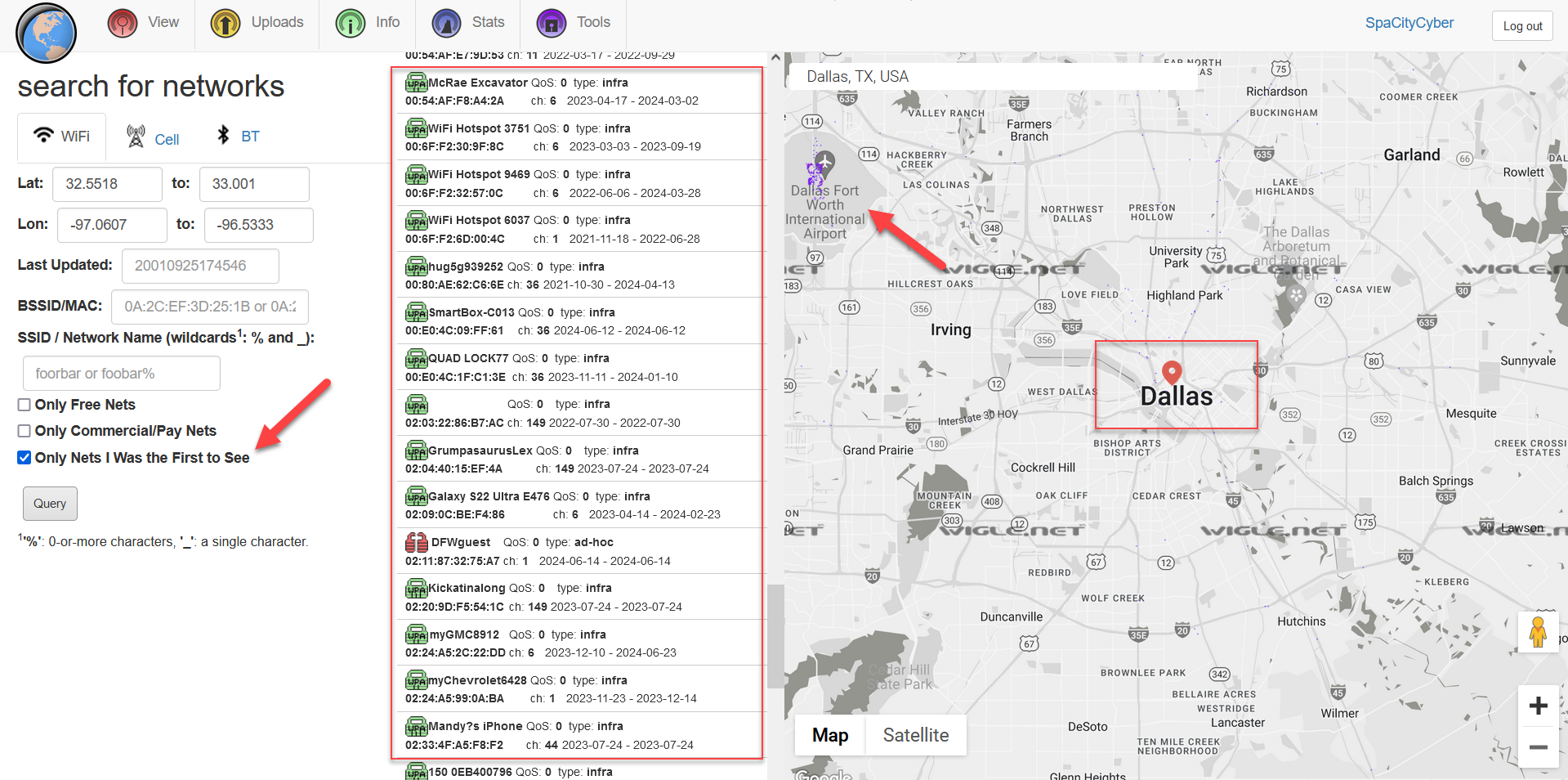
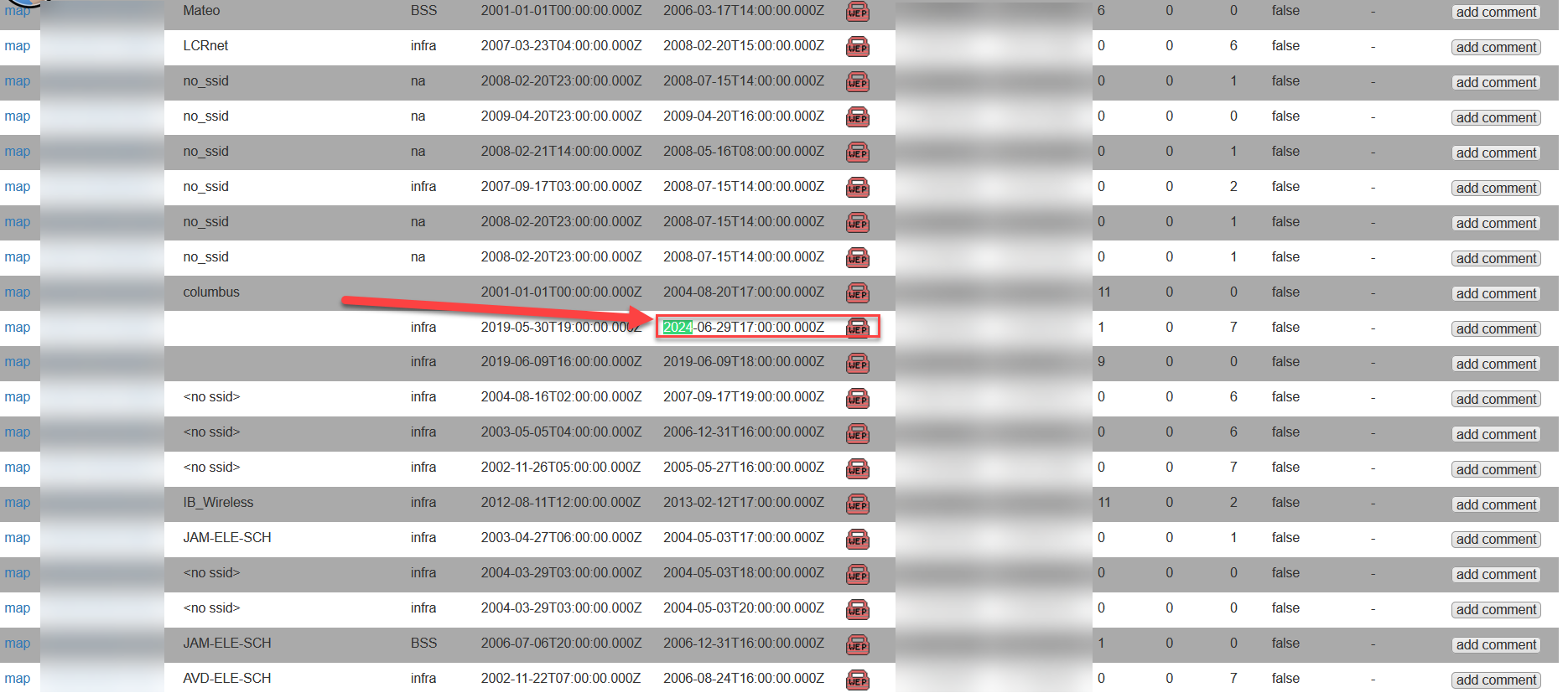
Now, this data is not aggregated by name since two unrelated individuals on two different sides of the world can call their network "FBI Surveillance Van". However, information for the same BSSID is aggregated. If a BSSID is captured and uploaded more than once over a period of time, this information is stored under the same ID, which allows you to view changes to a network over time. For example, you may be able to track certain BSSIDs changing from WPA to WPA2, or switching from supporting WPS to having WPS disabled. You can also track name changes.
The next feature is the advanced search. You can use this to search an area for networks supporting older encryption. For instance, if you're targeting a manufacturing facility that you suspect has older Wi-Fi equipment in use, why not leverage it for network access?
Some Pre-Reqs
There are several ways one could accrue data to upload to Wigle or collect for offline analysis, such as a wireless site survey (a crucial part of a good Wi-Fi pentest). As mentioned above, it's possible to use an Android app. Airodump-ng is written to support working with GPSD for this purpose as well. However, one of the most powerful tools for collecting signal and location data simultaneously is Kismet. Kismet has support for all sorts of signals, however we are going to focus on Wi-Fi, specifically the 6 GHz band.
We won't cover installing Kismet, GPS tools, or installing drivers for adapters for now. However, we'll provide an inventory list to get started:
- A laptop with virtualization software
- Alfa Networks AWUS036AXML & compatible 6 GHz tuned antennas
- A VNA if you did not purchase the antennas directly from Rokland or another legitimate Alfa reseller
- A USB GPS dongle
- Linux distribution with support for the mt7921au chipset, running in a VM. Kali is recommended at the current time of writing due to ease of use
- Kismet and dependencies
Once you have all of the necessary software installed, ensure your GPS dongle has downloaded it's almanac data and locked on to satellites. You can check this by running gpsmon -n and look for a message stating 3D Fix. It's suggested to keep the GPS dongle outdoors or near an open window to download almanac data, as it can take 20 minutes or more. When this has finished, you're ready to configure Kismet for picking up 6 GHz signals.
Configuring and Running Kismet
Getting ready to capture 6 GHz signals is fairly straightforward. You'll need to ensure that the 6 GHz band is available to your system, run sudo iw reg set US. Modify the primary config file: /etc/kismet/kismet.conf and add the following line source=wlan0:name=axe,band24ghz=false,band5ghz=false,band6ghz=true,channel=1w6e. Here's a breakdown of these parameters:
- source - The NIC you're using to capture signals.
- name - Whatever you would like to call the interface in Kismet.
- bandxghz - Configures the frequency band to operate on. We're excluding 2.4 and 5 GHz to target 6 GHz only.
- channel - This specifies channels the card will operate on. Each frequency band is divided into operating channels.
There are other parameters available if you would like to tune this further, just check out the Kismet documentation. Now that this is configured, let's run Kismet in Wardrive mode. Essentially, this mode saves power as it's monitoring for less information and outputs captured information to a format we can upload directly to Wigle. We'll do this with sudo kismet --override wardrive.
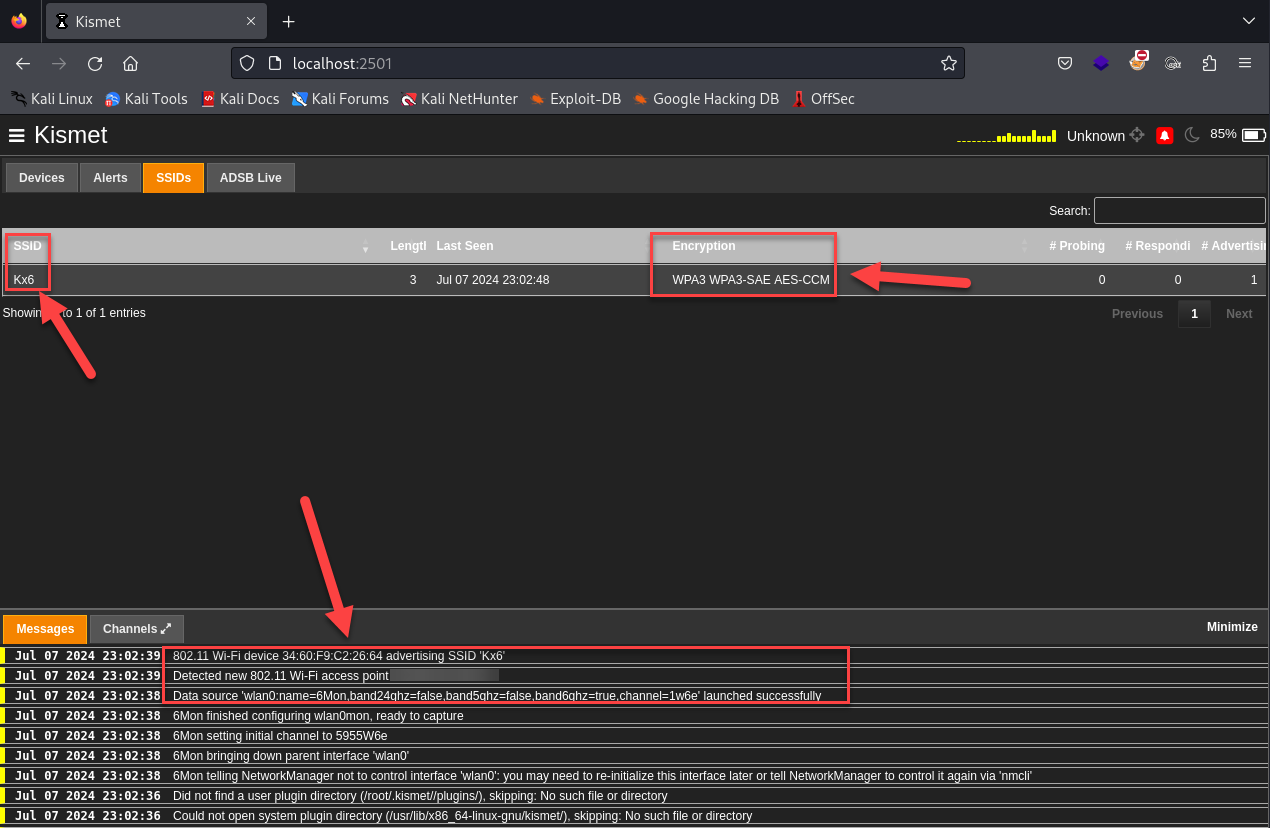
There we have it! Now you're ready to start wardriving on the 6 GHz band. If you elect not to use the --override wardrive option and only get a .kismet file, there's a built-in tool to transform this to a usable format for Wigle. Just run sudo kismetdb_to_wiglecsv --in xxx.kismet --out whatever.csv.
Next Up
The plan was to cover some defensive Wi-Fi tooling in this post, but we don't want you to fall asleep reading! So keep an eye out for our next post in the wireless series where we'll introduce Nzyme.
